Configure Virtual Connector
Virtual Magic WAN Connector (Virtual Connector) is a virtual appliance alternative to the hardware based Magic WAN Connector appliance. These two versions of Connector are identical otherwise.
Prerequisites
Before you can install Virtual Connector, you need an Enterprise account with Magic WAN enabled. Additionally, you need to have a VMware host with sufficient compute, memory, and storage to run the virtual machine with Virtual Connector. This includes:
- Intel x86 CPU architecture
- ESXi hypervisor 7.0U1 or higher
- 4 virtual CPUs per virtual connector (We recommend deployment with a 1:1 virtual CPU to physical core allocation to avoid CPU over contention which will cause packet loss.)
- 4 GB of RAM per virtual connector
- 8 GB of disk per virtual connector
- One vSwitch port group or VLAN with access to the Internet (for example, through a WAN)
- One or more vSwitch port group or VLAN that will be the internal LAN
Refer to VMware’s documentation for more information on how to install ESXi and configure a virtual machine.
1. Obtain the Virtual Connector image
Contact your account team at Cloudflare to obtain the Virtual Connector OVA package and license keys. The OVA image includes the files required to install and configure the virtual machine (VM) for Virtual Connector with the appropriate settings.
This image can be deployed multiple times to create several instances of a Virtual Connector, in different locations or on the same ESXi host.
You will consume one license key for each instance created. For example, if you want to deploy 10 Virtual Connectors you should request 10 license keys, and your account team will create 10 Connector instances in your Cloudflare dashboard.
2. Deploy the Virtual Connector on VMware
The following instructions assume you already have VMware ESXi hypervisor installed with sufficient resources. Refer to Prerequisites for more information.
When setting up your VMware ESXi, you need to create port groups for Virtual Connector. Go to Networking > Port groups, and prepare your vSwitch port groups and/or VLANs for your desired network topology. For example, a simple deployment typically has:
- A WAN port group where the Virtual Connector will get an IP address (static or DHCP) that has access to the Internet.
- A LAN port group, where the Virtual Connector will act as default router, and possibly DHCP server.
- A null, or unused, port group for allocating unused virtual interfaces in the Virtual Connector. You can, for example, create a null port group with the name of
Null port group, and a VLAN ID of999.
Extract the files in the OVA image provided by your Cloudflare account team. For example:
tar -xvf mconn-2024-1-3.ovaTake note of the folder where you are extracting the files to, as you will need to refer to that folder when creating the VM.
Go to Virtual Machines > Create/Register VM wizard to start deploying the Virtual Connector.
Select Deploy a virtual machine from an OVF or OVA file > Next.
Choose a descriptive name for your virtual machine.
Upload the files you have extracted from the OVA image. These include
mconn.ovf,mconn.nvram, andmconn.vmdk.Select where you want to save the files extracted from the OVA image > Next.
In Networking mappings, select assignments for your desired topology according to the port groups you set up previously:
- For example, map
eno1port toVM Networkto create your WAN, andeno2toLAN0to act as your LAN port. - Allocate any unused ports to the
nullport group. - Take note of your configuration. You will need this information to configure your network in the Cloudflare dashboard.
- For example, map
In Disk provisioning, select Thin.
Before completing the deployment wizard, disable Power on automatically. This is important so that you can configure the license key prior to boot.
Configure the virtual machine with the license key your account team provided you:
- Select the Virtual Connector’s VM > Settings.
- Go to VM Options > Advanced > Edit Configuration.
- Select Add parameter to add your license key. Scroll down to the last entry (this is where VMware adds the new parameter), and add the following two new entries:
- Key:
guestinfo.cloudflare.identity - Value:
<YOUR_LICENCE_KEY>
- Key:
- Select Save to finish configuring your Virtual Connector.
- Continue set up in your Cloudflare dashboard.
3. Set up Cloudflare dashboard
1. Create a site
Sites represent the local network where you have installed your Magic WAN Connector — for example, a branch office location.
You need to create a site and set up all the settings associated with it before you can connect your Magic WAN Connector to the Internet.
To add a site:
- Log in to the Cloudflare dashboard and select your account.
- Go to Magic WAN > Sites.
- Select Create to create a new site and start the configuration wizard.
- Add a name and description for your new site.
- Under Connector, select Add Connector. This will show you a list of Magic WAN Connector devices associated with your account. For a Virtual Connector to show up you need to have already obtained your OVA package and licence keys.
- If you have more than one Connector, choose the one that corresponds to the site you are creating. Connectors are identified by a serial number, also known as a service tag. Use this information to choose the right Connector. Select Add Connector when you are ready to proceed.
- The Connector will be added to your site with an Interrupt window defined. The interrupt window is the time period when the Magic WAN Connector software can update, which may result in interruption to existing connections. You can change this later. Refer to Interrupt window for more details on how to define when the Connector can update its systems.
- Select Next to proceed to creating your WAN and LAN networks.
2. Create a WAN
- In WAN configuration, select Create. You can create one or more wide area networks (WANs). Configuring multiple WANs will create multiple IPsec tunnels. This allows the Connector to failover between circuits according to their health.
- In Network name, enter a descriptive name for your WAN.
- In VLAN ID, enter a number between
0and4094to specify a VLAN ID. - Physical port needs to correspond to the virtual network interface on the Virtual Connector instance you have set up in VMware. Following our example from the previous steps, you need to choose port
1since that is what corresponds to theeno1port we set up in VMware. - In Priority, choose the priority for your WAN. Lower numbers have higher priority. Refer to Traffic steering to learn more about how Cloudflare calculates priorities.
- Addressing: Specify whether the WAN IP is fetched from a DHCP server or if it is a static IP. If you choose a static IP, you also need to specify the static IP and gateway addresses.
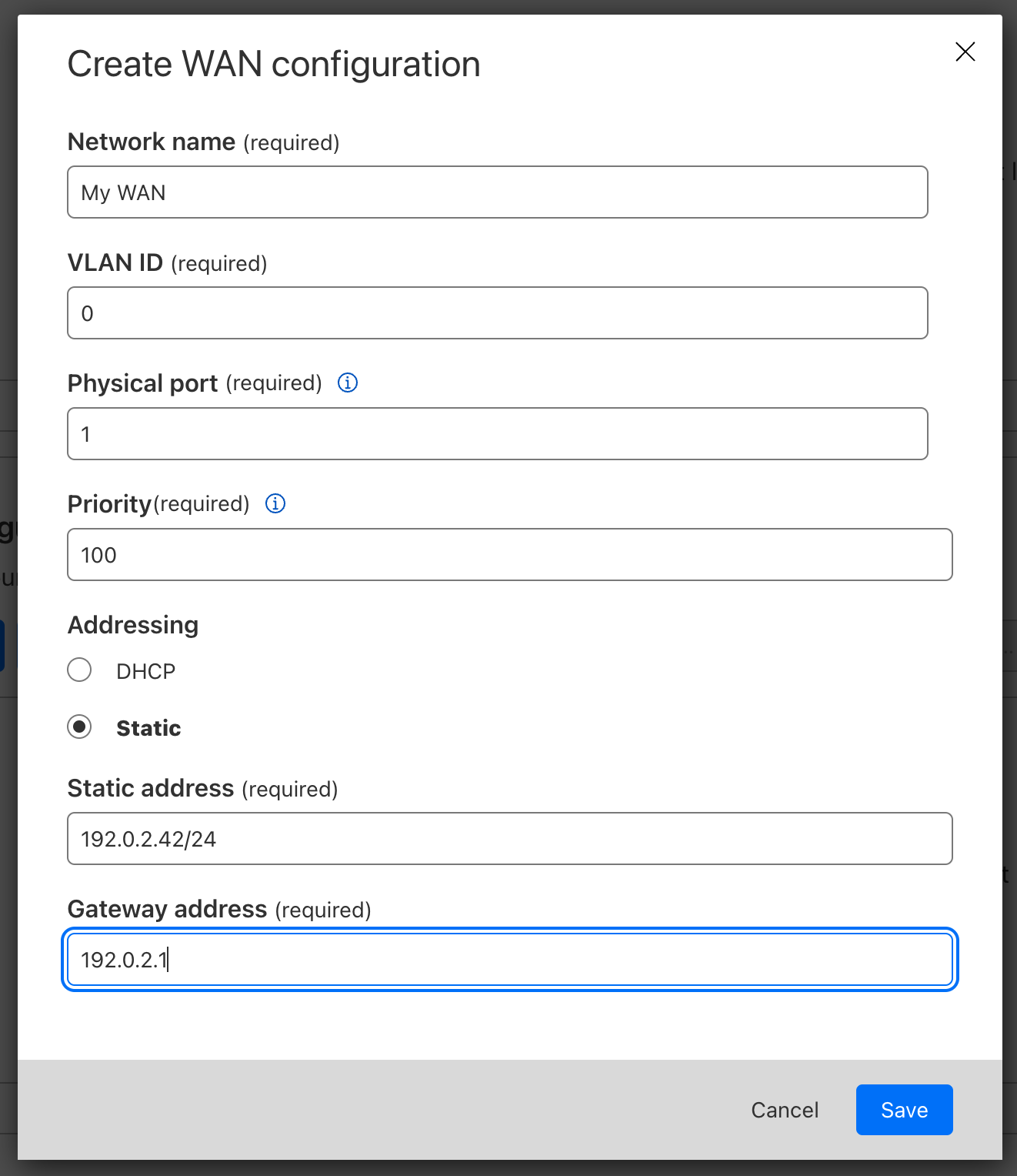
- Select Save when you are finished.
3. Create a LAN
In LAN configuration, select Create.
Enter a descriptive name for your LAN in Network name.
Physical interface needs to correspond to the virtual LAN interface on the Virtual Connector instance you have set up in VMware. Following our example from the previous steps, you need to choose port
2since that is what corresponds to theeno2port we set up in VMware.In VLAN ID, specify a VLAN ID to create virtual LANs.
In Static addressing > Static address give your Connector’s LAN interface its IP address. You can also enable the following options if they suit your use case:
- This is a DHCP server: If your Connector is a DHCP server.
- This is a DHCP relay: If your Connector is a DHCP relay.
(Optional) In Directly attached subnet > Static NAT prefix, enter a CIDR prefix to enable NAT (network address translation). The prefix you enter here should be the same size as the prefix entered in Static addressing. For example, both networks have a subnet mask of
/24:192.168.100.0/24and10.10.100.0/24.(Optional) If your LAN contains additional subnets behind a layer 3 router, select Add routed subnet under Routed subnets to add them:
Prefix: The CIDR prefix for the subnet behind the L3 router.
Next hop: The address of the L3 router to which the Connector should forward packets for this subnet.
Static NAT prefix: Optional setting. If you want to enable NAT for a routed subnet, supply an “external” prefix for the overlay-facing side of the NAT to use. It must be the same size as Prefix.
Refer to Routed subnets for more information.
Select Save.
Select Save and exit to finish your configuration. Tunnels and static routes will be automatically created and associated with your site once the Magic WAN Connector boots up (refer to the next step).
Network segmentation
After setting up your LANs, you can configure your Connector to enable communication between them without traffic leaving your premises. Refer to Network segmentation for more information.
DHCP options
Magic WAN Connector supports different types of DHCP configurations. Connector can:
- Connect to a DHCP server or use a static IP address instead of connecting to a DHCP server.
- Act as a DHCP server.
- Use DHCP relay to connect to a DHCP server outside the location your Magic WAN Connector is in.
- Reserve IP addresses for specific devices on your network.
Refer to DHCP options to learn more.
4. Activate Connector
Virtual Magic WAN Connector is deactivated after you install it, and will only establish a connection to the Cloudflare network when it is activated. Cloudflare recommends leaving it deactivated until you finish setting it up in the dashboard.
When the Connector is first activated, one of the ports must be connected to the Internet through a device that supports DHCP. This is required so that the Connector can reach the Cloudflare global network and download the required configurations that you set up in the site configuration step.
When you are ready to connect your Magic WAN Connector to the Cloudflare network:
- Log in to the Cloudflare dashboard and select your account.
- Go to Magic WAN > Configuration > Connectors.
- Find the Connector you want to activate, select the three dots next to it > Edit. Make sure you verify the serial number to choose the right connector you want to activate.
- In the new window, the Status dropdown will show as Deactivated. Select it to change the status to Activated.
- The Interrupt window is the time period when the Magic WAN Connector software can update, which may result in interruption to existing connections. Choose a time period to minimize disruption to your sites. Refer to Interrupt window for more details on how to define when the Connector can update its systems.
- Select Update.
5. Boot your Virtual Connector
- Go to Virtual Machines in VMware, and boot up Virtual Connector’s VM.
- The Virtual Connector will make a request to Cloudflare. This is the step where Virtual Connector registers your provided license key and downloads the site configuration for its connected site.
- The Virtual Connector will set up the LAN and WAN connections according to the configuration downloaded from the site you created on the Cloudflare dashboard. The Virtual Connector will also establish IPsec tunnels.
- If successful, the tunnel health checks will show as healthy.
- If you do not see a healthy heartbeat the Cloudflare dashboard, reboot the Virtual Connector’s VM in VMware.
IP sec tunnels and static routes
Magic WAN Connector automatically creates IPsec tunnels and static routes for you. You cannot configure these manually.
To check the IPsec tunnels and static routes created by your Magic WAN Connector:
- Log in to the Cloudflare dashboard and select your account.
- Go to Magic WAN > Sites.
- Select the name of the site for which you want to check the Connector’s IPsec tunnels and static routes, and select Edit.
- Select Tunnels to check IPsec tunnels, and Routes for the static routes.